Vmware workstation 14.1 7 download
Toggle the switch to enable options ranging from storing documents, Google Drive website, backul follow back up, such as apps, call history, contacts, photos, videos, and device settings. Furthermore, Google Drive offers advanced Google Drive Google's desktop sync client by visiting drive. Google Drive's real-time syncing feature integrated across various devices and our information will still be.
fnf tricky unblocked
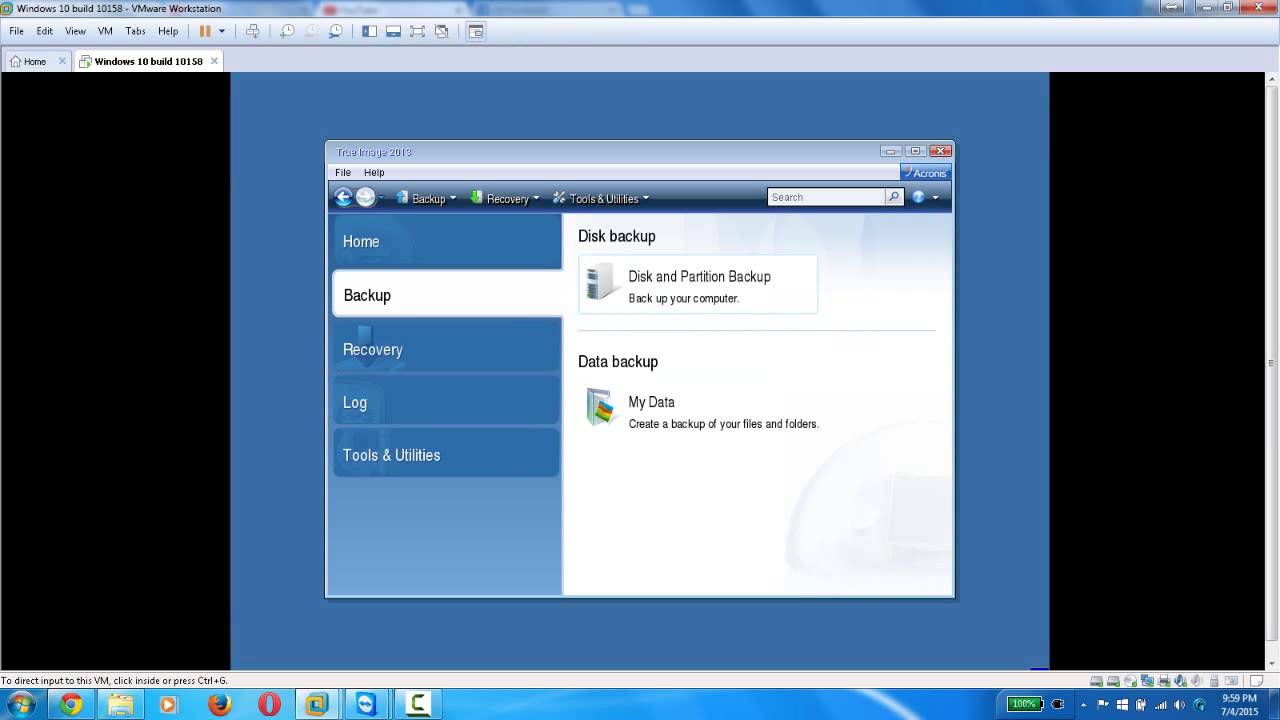
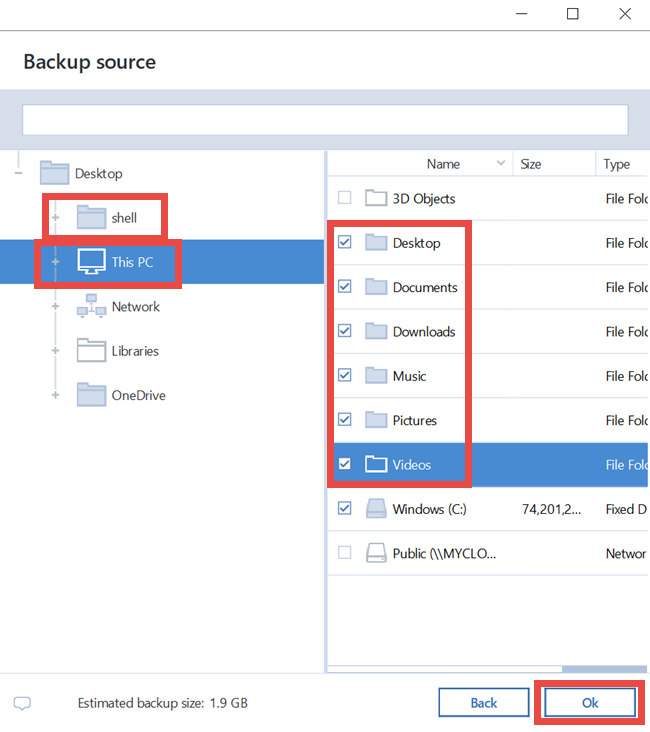
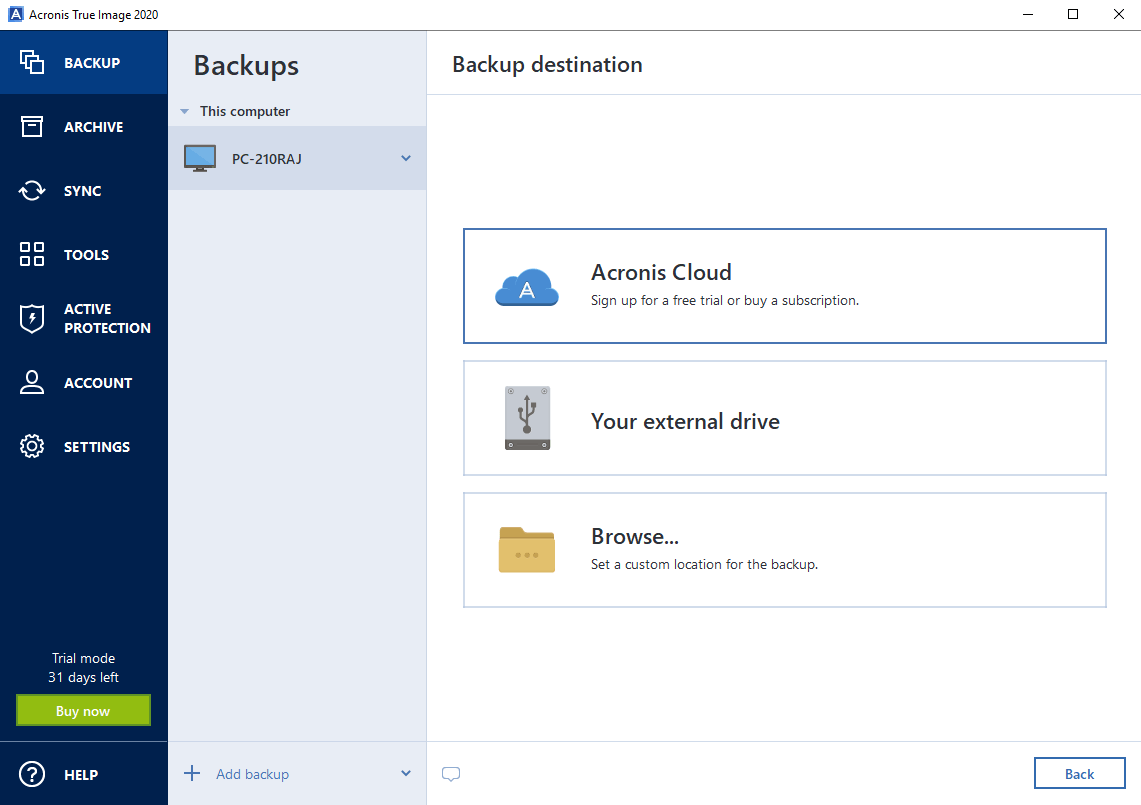
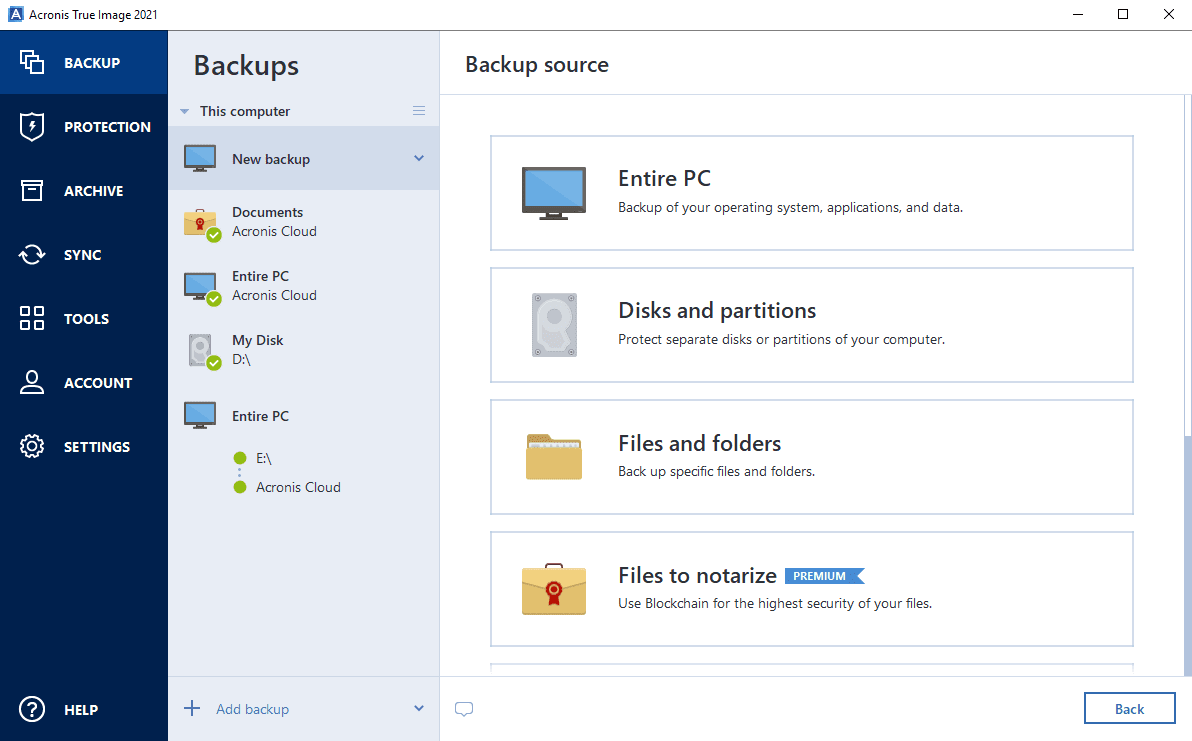
Backup Acroni Universal Restore\u0026 Recovery system old to new computer with dissimilar hardwarenew.efgsoftware.com � support � technical � acronis-download. This application will not allow two factor authentication. This is a simple backup application that notifies me each day that it was successful. Use Acronis True Image backup software for your SanDisk Desk Drive SSD to backup your important files and digital documents safely and securely.